🌐 Mirror, Mirror on the Net! 🕵️♂️ Unveiling the Astonishing IDS Port Mirror Project with ESP32 and Wireshark 🔍📊
Main index:
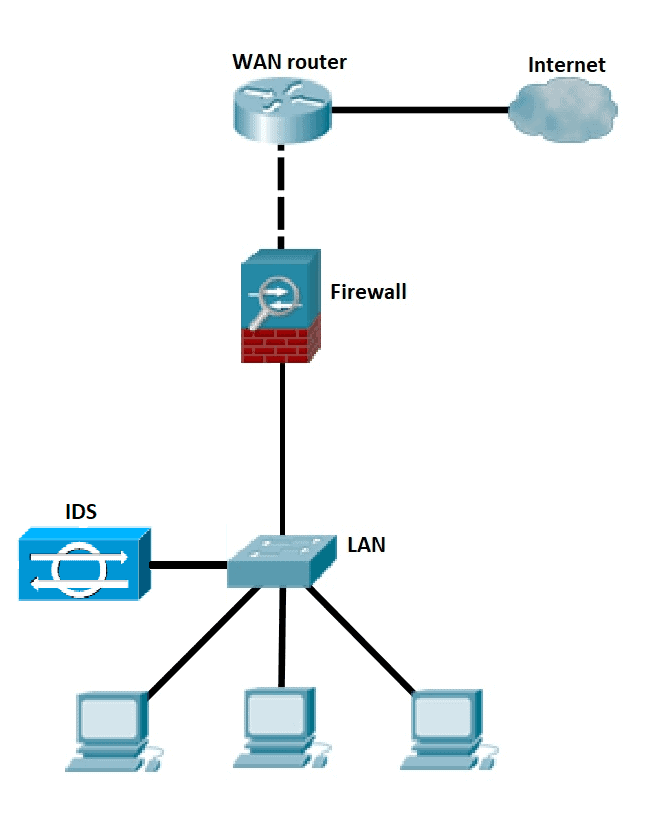
1. What is an IDS?
According to IBM's website, an IDS, is Intrusion Detection System. In which is a network tool which consists of monitoring traffic and also devices that may present malicious or suspicious activity, as well as devices that may violate security policies [2].
Its main function is in the analysis of network traffic, in which it is compared with signatures of known attacks or anomalous or suspicious behaviour, this type of analysis can be from a port scan, or interrupted or malformed packets. The disadvantage is that it cannot stop intruder packets on its own, but fortunately it has a built-in firewall that can also act as a packet blocker. [2].
Some types of IDS are categorised on the basis of what they can do, e.g. a NIDS (Network Intrusion Detection System), that its main function is to be behind the Firewalls so that if a packet gets past the Firewall then the NIDS blocks it.HIDS (Host Intrusion Detection Systems) are primarily installed on a specific modem or endpoint, such as a laptop, router, or server. It alone monitors activity on the device, including incoming and outgoing traffic [1][2][5].
2. What is Wireshark?
Wireshark works like an IDS, in this case it also analyses protocols and solves communication network problems. It has a graphical interface and also filters the information in a simple way, it can analyse the Ethernet, SSH, WIFI, etc. network. There is a command line version which is tshark [3].
3. What is IDS Port Mirror?
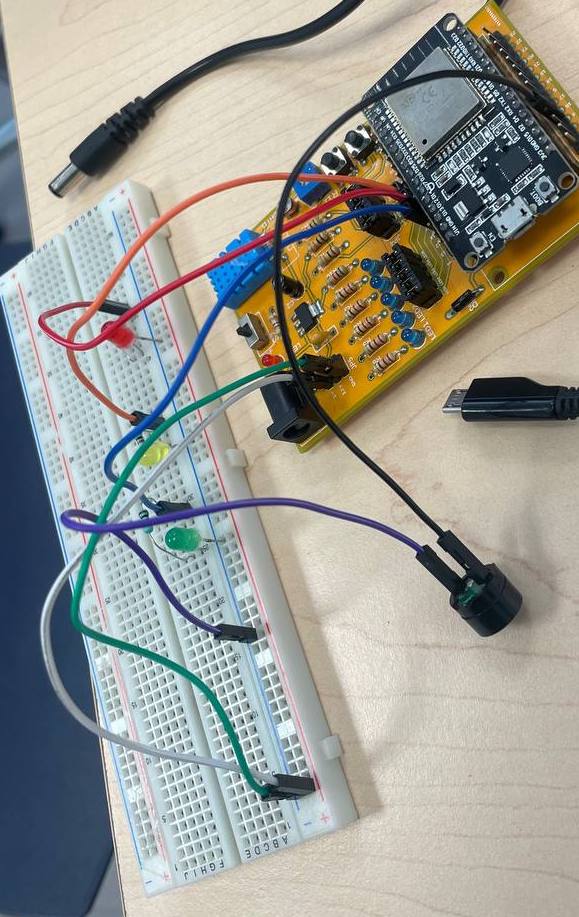
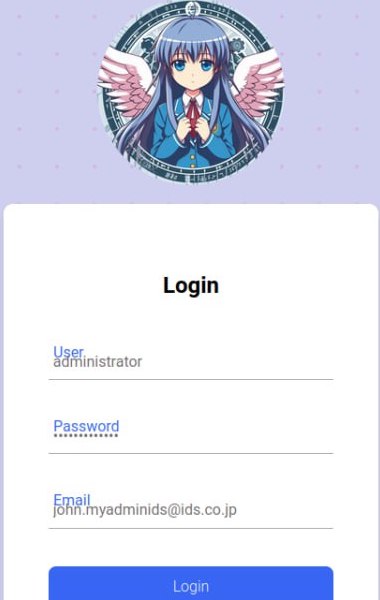
IDS Port Mirror is mainly a project about network analysis, acting as an IDS using several software and hardware tools. The latter uses an ESP32 which is practically a microcontroller in which it can have many functionalities, one of them being as an internal server (locally), WIFI, sending messages to Telegram, etc. To do this, it is worth mentioning that the memory of ESP32 is limited, which instead of acting as an IDS like Wireshark only pretends to be one, you could say that it is a HIDS, however, the operation does not only end here, with the help of Wireshark that can export in a . csv the traffic files, also with the help of Python and ShellScript, it was possible to receive the messages sent to a protoboard where it has 3 leds (red, yellow, green) plus a Buzzer (like a mini horn), it could also send mails (GMAIL) about the high logs of the network, and send notifications to Telegram (using a Bot Esp32NetworkTool).Finally, to see the time comparison of the logs that have been made, a database for the queries was implemented remotely using PHP on a page that is on the Instituto de Materiales de la UNAM (IIM – UNAM) The traffic could be visualised by using a login as an administrator. Each led had its functionality as shown in the following table:
| COMPONENTS | PIN - GPIO | FUNCTIONALITY |
| LED RED | 26 | If I turned it on, then I sent an email via Gmail to the network administrator, Telegram sends a notification. Finally, the buzzer sounds for a moment like an alarm. |
| LED YELLOW | 27 | If switched on, only Telegram sends a notification. |
| LED GREEN | 14 | It only turns on the LED when there is no suspicious activity. |
| BUZZER | 17 | It emits sound when the led is red. |
4. Python and ShellScript.
Python is a flexible programming language for someone who is just starting out in programming, however, Python cannot do all the work. In the IDS that was implemented in the ESP32, Python has one less point over the ESP32 (unless you modify the filmware with MicroPython), to get the data and also executing it from a terminal, like MetasPloit, it has the help of ShellScript, which is like the programming language that Linux operating systems have, so, anyone who has a Linux in his machine can program in both languages without difficulties because nowadays Python and Shell have good communion at the moment of executing processes. He left a couple of videos about ShellScript and Python from one of my favourite Youtubers in security and networking.
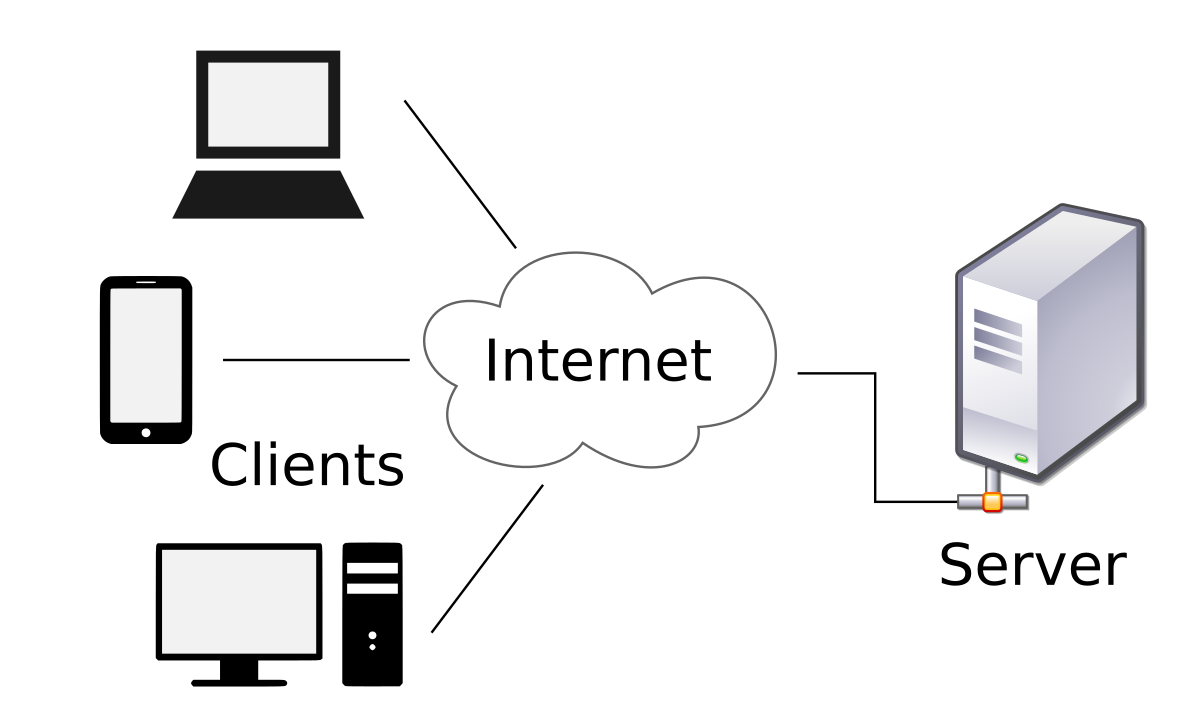
5. Client-Server Architecture.
It is important to talk about this architecture as it was used for monitoring and receiving and sending data. This model consists of communication between the services, which we will call servers, and also the requestors, which we will call clients. The client makes a request to another program and the server gives a response [4]. An example is when you search for kittens on Google, and when you click on a page you expect to get access to see those kittens. In a simple way is the explanation of this model. For the IDS the communication between four services (Gmail, Telegram, Server(ESP32), web server) and the client was maintained.
6. Previous projects.
This project was not the only one, but there were also other people who were able to modify the ESP32 without any external software to act as an IDS, like in the case of ArduinoPcap.
7. Conclusions.
In conclusion, an IDS is an excellent option for the traffic of information when you want to analyse, besides this project works as a Mirror Port, in this case it does not have a Switch but it simulates with the computer to have one and to see the traffic filtered by an IP that has the ESP32 and also by the computer connecting remotely to a server to interact with it and likewise, to go filling data with a simple base, that later can be visualised. If you want to see the project in a more detailed way, here is the repository that contains it IDS Port Mirror. If you liked the project, give a 🌟 to the repository.


1.The logo design was inspired by Yuri and Angel from Angels Beats! using an AI.
2.Angel Beats! | Nakamura Yuri | Tachibana Kanade | Pinterest.
8. Acknowledgement.
9. References.
What is an intrusion detection system (IDS) (N/A). IBM. Accessed on: 15:00, November 10, 2023 from What is an intrusion detection system (IDS)?
Intrusion detection system (2023, 7 July). Wikipedia, The free encyclopedia. Accessed: 18:11, October 7, 2023 from Intrusion detection system.
Wireshark (2023, 17 November). Wikipedia, The free encyclopedia. Accessed on: 21:22, November 17, 2023 from Wireshark.
Client-server (2023, 20 October). Wikipedia, The free encyclopedia. Access date: 23:05, October 20, 2023 from Client-server.
Cisco IDS/IPS Fundamentals (2020, 15 February). The Cisco Learning Network. Access date: 19:00, November 31, 2023 from Cisco IDS/IPS Fundamentals.